VPC-Only Access
The VPC-only access feature provides enhanced security for your Kubernetes clusters by disabling the public endpoint for the cluster control plane. When enabled, the Kubernetes API server can only be accessed from within the VPC, requiring users to establish secure connectivity through VPN or bastion host solutions.
Overview
By default, Kubernetes clusters are accessible from the internet through a public endpoint. While this provides convenience for cluster management, it may not meet the security requirements of all organisations. The VPC-only access feature addresses this by restricting cluster access to only those resources within the same VPC.
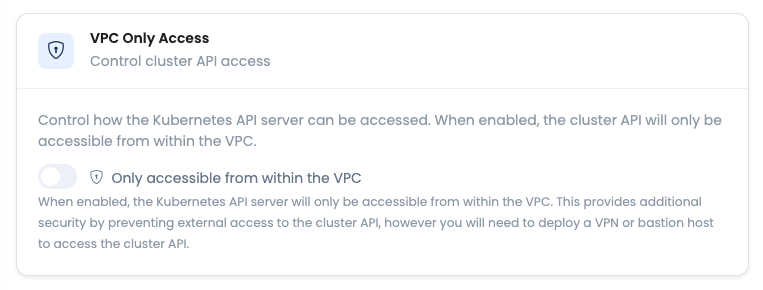
Enable / Disable VPC Only Access for Kubernetes Control Plane
How It Works
When VPC-only access is enabled:
- The public endpoint for the Kubernetes control plane is disabled
- The cluster API server is only accessible from within the VPC
- External access requires establishing connectivity through the VPC
Configuration
The VPC-only access feature is controlled by the DisablePublicEndpoint API field:
- Default value:
false(public endpoint enabled) - VPC-only access: Set to
trueto disable public endpoint
Access Methods
When VPC-only access is enabled, you can access your Kubernetes cluster through:
- VPN Connection: Deploy a VPN solution within your VPC to establish secure connectivity from your local environment.
- Bastion Host: Deploy a bastion host or jump server within the VPC that acts as a gateway for cluster access.
- VPC Peering: If you have multiple VPCs, configure VPC peering to allow access from other VPCs.
Current Limitations
Kubernetes Dashboard
Due to the public endpoint being disabled, the Kubernetes Dashboard functionality within the cloud console is currently unavailable when VPC-only access is enabled. This limitation will be resolved in a future update.
Troubleshooting
Cannot Access Cluster
If you cannot access your cluster after enabling VPC-only access:
- Verify your VPN or bastion connection is established
- Check that your local IP is within the allowed VPC range
- Ensure security groups allow traffic from your source
- Verify network routing is properly configured
Verify Security Groups or VPC ACLs
If you have configured security groups on your Control Plane, ensure it allows access from your endpoint (VPN, Bastion, etc). Likewise, dubble check your VPC Firewall Rules / ACLs.